In today’s digital age, building secure applications is no longer optional — it’s essential. With increasing threats like data breaches, ransomware, and code injection attacks, businesses must adopt a “secure by design” approach from the very first line of code. For companies like Zappkode Solutions, security isn’t just a feature — it’s a foundation.
This blog will guide developers, architects, and decision-makers on how to build secure applications from day one, covering best practices, tools, and strategies for integrating security into every stage of the software development lifecycle.
Why Security from Day One Matters
Starting with security early ensures:
- Reduced risk of vulnerabilities in production
- Lower cost of fixes compared to post-release patches
- Increased customer trust and compliance with regulations (e.g., GDPR, HIPAA)
- Avoidance of reputation damage and financial losses
Start with a Secure Software Development Lifecycle (SSDLC)

Implementing a Secure Software Development Lifecycle (SSDLC) means embedding security at each stage — from planning to deployment.
Key Steps:
- Threat modeling during planning
- Secure architecture design
- Code reviews focused on vulnerabilities
- Security testing before release
Companies like Zappkode Solutions can enhance their development process by adopting SSDLC practices, ensuring that security is built into the foundation of every product.
Follow Secure Coding Best Practices
Secure applications start with secure code. Developers must be trained and encouraged to follow industry-approved coding standards such as those provided by OWASP.
Secure Coding Practices:
- Avoid hard-coded credentials
- Sanitize all inputs (to prevent SQL injection and XSS)
- Use prepared statements and parameterized queries
- Validate data on both client and server sides
Use Secure Frameworks and Libraries
Modern frameworks often come with built-in security features. However, it’s vital to:
- Keep frameworks and dependencies up to date
- Avoid using outdated or unmaintained libraries
- Use vulnerability scanners like Snyk, Dependabot, or OWASP Dependency-Check
At Zappkode Solutions, integrating tools like these into CI/CD pipelines helps ensure software remains secure as it evolves.
Perform Regular Threat Modeling
Threat modeling helps identify potential security risks in the design phase before they become real problems.
Recommended Tools:
- Microsoft Threat Modeling Tool
- OWASP Threat Dragon
- Lucidchart or Draw.io (for architecture diagrams)
This approach empowers development teams to think like attackers and strengthen weak points early.
Apply Strong Authentication & Authorization
Authentication (who the user is) and authorization (what they can access) are crucial to application security.
Best Practices:
- Implement Multi-Factor Authentication (MFA)
- Use OAuth2, OpenID Connect for secure identity management
- Role-based access control (RBAC) for managing user permissions
Zappkode Solutions can integrate these protocols to protect user data and limit exposure to unauthorized access.
Encrypt Sensitive Data
Encryption ensures that even if data is stolen, it remains unreadable to attackers.
Key Encryption Guidelines:
- Use HTTPS/TLS for all data in transit
- Encrypt sensitive data at rest using AES-256 or similar standards
- Store passwords using hashing algorithms like bcrypt or Argon2
Encryption should be a default, not an afterthought, in all Zappkode Solutions projects.
Integrate Security into DevOps (DevSecOps)
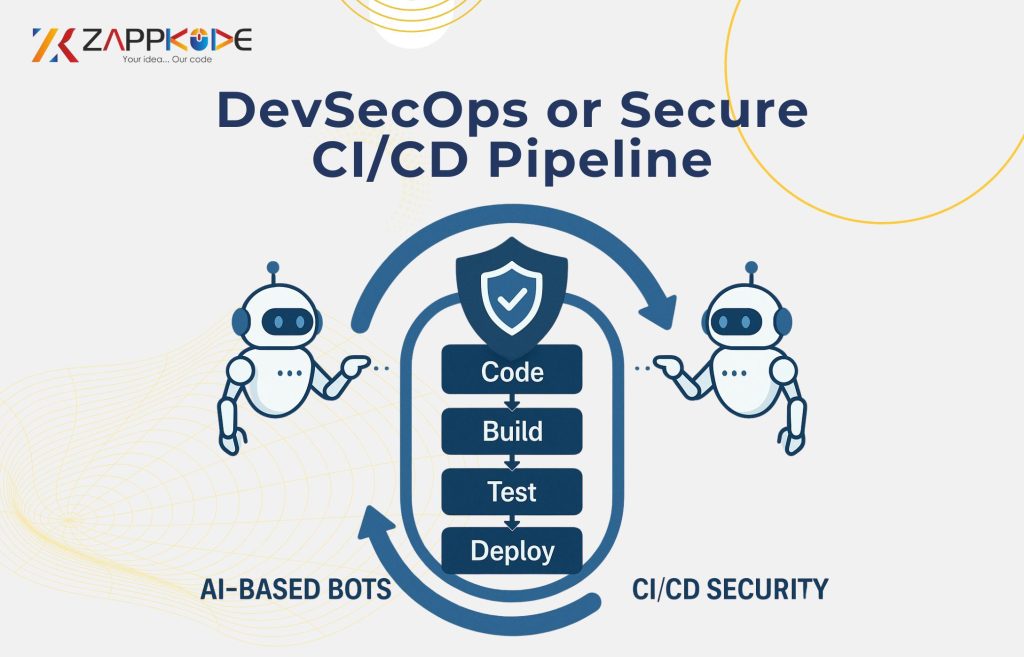
DevSecOps brings security into the DevOps pipeline, making it part of continuous integration and continuous deployment (CI/CD).
Practices:
- Run static analysis (SAST) and dynamic analysis (DAST) tools automatically
- Scan for secrets in code before committing
- Automate security tests during deployment
Tools like SonarQube, Checkmarx, Veracode, and GitHub Advanced Security can be used.
Zappkode Solutions can gain significant efficiency and reduce post-deployment vulnerabilities by making security part of their DevOps process.
Conduct Regular Security Audits and Penetration Testing
Even with the best practices, it’s vital to test the system like a real attacker would.
Recommended Activities:
- Schedule regular penetration tests
- Perform vulnerability assessments
- Use bug bounty programs for crowd-sourced security testing
Educate Your Development Team
Security is a shared responsibility. Developers, testers, and managers all need to understand secure development principles.
Methods:
- Conduct regular security training
- Share secure coding cheat sheets
- Encourage secure code reviews and peer audits
At Zappkode Solutions, internal training sessions can ensure the entire team is aligned on cybersecurity goals.
Monitor, Log, and Respond
After deployment, it’s crucial to monitor application activity for any unusual behavior.
Key Components:
- Centralized logging using tools like ELK Stack, Datadog, or Splunk
- Real-time alerts for intrusion attempts
- Incident response plans in place
With robust monitoring, Zappkode Solutions can detect and respond to threats before they cause damage.
Final Thoughts: Zappkode’s Commitment to Secure Applications
In a world where cyber threats evolve daily, Zappkode Solutions remains committed to delivering secure, scalable, and reliable software solutions. By adopting a security-first mindset from day one, we help clients build digital products that customers trust and hackers fear.
Whether you’re building a mobile app, web platform, or enterprise system — start secure, stay secure.